-

NFT for Christmas
So this beautiful NFT or Non Fungible Token was one of the price for SANS Kringlecon Virtual Event, a cyber security challenge and virtual conference. Feel free to deposit Kringlecoin in my wallet if you liked this article or want to make an offer for this piece of art1. This year was lord of the ring themed and I’ll talk more in depth about my favorite track that was about CI/CD (Continuous Integration / Continuous Delivery). But first I would briefly talk about another fun event during the Christmas holiday: TryHackMe advent of cyber
-
Not my NFT, not my wallet and not a real cryptocurrency. ↩
-
-

United CTF 2022
Last year I was supposed to do a post on UnitedCTF web challenge but I ran out of gas. Too bad there was tons of cool stuff: a series of file upload challenges, a website featuring a cute dog, a pentest on a fake government website and hacking techniques based on the Vaxicode mobile app. In this post I’ll show you how I combined SQL injection and XSS, an introductory mobile app pentest and one thing I learned about DNS. I will also talks about the track made by Desjardins, which was my favorite this year. As always the challenge are available on Github so you can try them yourselves
-
Northsec Hackademy
What’s worst then a half baked poorly written writeup? My writeup, of course! Just kidding but I’ve updated it so it will be easier to use. It’s a beginner track so you want to try it by yourself first but sometimes if you’ve never seen the technique, reading the solution while doing it might be another great way to learn.
-
UnitedCTF 2021 part 4: QR and cats
Crypto and steganography are definitely not my specialty but I checked them out to see if there was some low hanging fruits. I checked the ones who were not worth a lot of points but I also looked at the number of peoples who had solved the challenge. Here are some that I’ve done:
-
UnitedCTF 2021 part 3: ReDoS
That track was very interesting for me because I didn’t knew what ReDoS was and it turns out it’s pretty powerful. So ReDoS means Regular expression Denial of Services. Basically there is some kind of algorithm that will try to match a string with the regular expression by evaluating all the possible paths. So you craft a string that will not match the regular expression but that will have a lot of possibility for the algorithm to explore.
-
UnitedCTF 2021 part 2: SQL injection
I really liked this track, there was nine (relatively) easy challenges on SQL injection. There was a thorough explanation on how to do the first challenge and it allowed everyone to catch up and brush up their skills. Since I’ve already talked about SQL injection in a previous blog I’ll skip right to the chase.
-
UnitedCTF 2021 part 1: Desjardins track (and more)
UnitedCTF is a Quebec university two week hacking competition that is open to all. It was the first time I participated and I was joined by a couple of my friends from Hackfest. I found it very beginner friendly, there was huge number of references and hints to help with the CTF and I managed to learn a couple of very interesting techniques.
-
NorthSec Wizard Academy
This year Northsec CTF was medieval themed and took place in the land of North Sectoria. In this kingdom, hackers are called magicians. Do you have what it takes to become a wizard?
-

NorthSec Capture The Flag preparation
I participated in Northsec 2021 CTF. It was super fun and the build up to it kept us pretty busy. I want to tell you about what the weeks were like up to the compettion. First I’ll talk about some of features and contents contained in this year badge. Then I’ll walk you through CTF warmup on the Discord that culminated in a mock hack on a public IP. After that, I’ll highlights some cool things I learned in the excellent CTF 101 workshop that I attended during the conference part of the NorthSec event. Finally, I’ll shortly describe my setup to connect to the IPv6 infra and I’ll show you where we find our first flag, before the event even started.
-

Auditing Wreath network
A new room has opened on Tryhackme to learn about network penetration testing: Wreath network. It’s a free room but you need to have a 7-day streak, meaning solving a question every day for seven days, to access it. The writeup for this room need to be in a different format than usual. You needed to write a penetration testing report as you would have to do if it was a real job. It was the first time for me so I had to learn more in details the classification of vulnerabilities and I had to put more toughts into potential remediation. My writeup got accepted and you can read it here: Penetration test report for Wreath network. In the rest of this post I’ll just highlights some of the things I found interesting.
-
Full database exfiltration oneliner
Now that I have your attention I must warn you, this post is about SQL injection. It’s been there for awhile and it’s widely known how to protect against them. But even then it’s still the top vulnerability in the OWASP top ten (even tough it been merged with other type of injection). You probably have seen this joke before (thanks to xkcd):
-
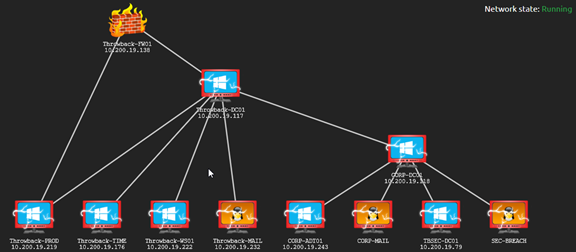
Pivoting through the Throwback Active Directory network
The Throwback network on Tryhackme simulate a realistic corporate Active Directory environment. In this scenario, you are part of a red team that is tasked to do a network penetration testing. Since this network is segmented I will be able to show you how to pivot from the DMZ to the first domain.